硬件和網絡安全:安心的第一步
在當今世界,關鍵領域的網路安全行動已日益普遍,專門的團隊直接保護各自公司的資產、聲譽以及最終利潤。然而,令人驚訝的是,工業環境中的網路安全卻常常被忽略。通常,專注於產品開發的設計部門或專注於應用的整合商,在面對邊緣或物聯網解決方案時,往往會無意中忽略所有必要的安全考量。
每年,科技業都會推出新的或升級的解決方案,包括增強連接性。互聯設備的趨勢旨在改善資料收集和自動化,我們對此表示全力支持。然而,網路安全必須從一開始就放在首位,從最初的設計需求文件開始就應該如此。在這個階段,我們會確定一些參數,這些參數會影響最終產品的組件選擇(如果您想了解更多規格信息,請閱讀我們的部落格)。 如何為邊緣應用選擇合適的單板計算機:決策指南 例如,雖然看似無害,但諸如USB連接埠數量之類的決定可能會無意中造成安全漏洞。選擇僅配備必要USB連接埠的平台可以最大限度地降低這種風險。在軟體/韌體方面,系統BIOS和啟動過程也應仔細考慮並做好記錄。
有人可能會認為,對於小批量部署而言,客製化硬體解決方案在經濟上並不划算。在這種情況下,供應商可以提供專業知識,對標準產品進行「客製化」。例如,Contec 的 BX-M2500 盒式電腦(造訪我們的網站) 網上商店頁面此功能允許使用者透過選擇多種配置選項來配置 USB 連接埠(請參閱圖 1)。此功能與 BIOS 密碼保護相結合,可顯著提高安全性。
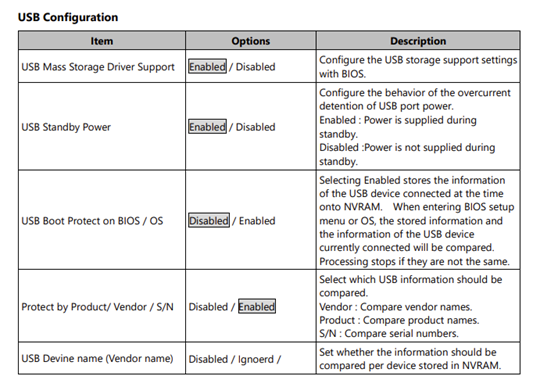
圖 1. BX-M2500 系列參考手冊摘錄。
這個例子突顯了網路安全因素如何影響硬體選擇。其他重要因素包括設備的實體位置。將裝箱的電腦放置在生產線上,可能會使其面臨被篡改的風險,並可能損害資料完整性。網路安全的最終目標是保護數據,而工業環境中的數據形式多種多樣。例如,必須確保感測器與電腦正常通信,並且演算法按預期運行,從而實現保護資料的目標,使演算法能夠正常運行並產生預期的操作和結果。
在解決方案中,安全機箱的重要性有時會被忽略。此組件不僅能保護設備免受惡劣環境的侵害,還能抵禦網路犯罪者的攻擊。例如,如今我們正處於人工智慧時代,對高階運算能力的需求與日俱增。 Nvidia 的 Jetson 平台在這方面表現出色,它包含小型、節能的模組和開發套件,可為邊緣生成式人工智慧提供支援。然而,僅僅依賴 SDK 或模組作為最終解決方案是不夠的;還需要其他功能來確保可靠性。可靠性的一部分取決於機箱,它作為第一層安全防護,提供物理屏障(通常包含入侵檢測功能),防止他人輕易物理接觸模組,並在硬體遭到入侵時發出警報。 Contec 機箱電腦還包含多種使其成為更強大解決方案的功能,例如寬輸入電壓範圍、耐高溫和耐塵環境、標準認證等等。在考慮網路安全需求時,必須考慮實體存取設備可能造成的後果。選擇合適的硬體是建立安全系統的第一步。請在我們的網上商店查看Nvidia Jetson。)
最後,還有其他一些安全特性值得關注,例如可信任平台模組 (TPM)、硬體安全模組 (HSM) 和 UEFI 安全啟動,它們透過增強作業系統來提高安全性(更多資訊請參閱我們的部落格)。 從硬體角度看邊緣安全透過在硬體選擇中優先考慮網路安全,企業可以降低資料遺失和聲譽受損的風險和成本。閱讀我們的部落格“5 個關於如何對設施進行硬體加固的技巧如需了解更多關於如何最大限度降低您設施風險的資訊。
在日益互聯互通和自動化的世界中,保護資料和系統始終是一項挑戰。然而,投入更多的時間和資源來設計安全解決方案,並充分考慮網路安全因素,將顯著降低網路攻擊的風險,讓您和您的客戶安心無憂。



